بایگانی برچسب برای: Cisco
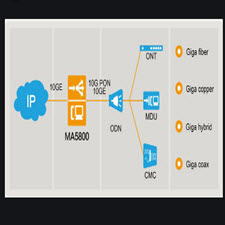
معماری MPLS
اطلاع رسانی
طرح سوییچینگ برچسب چند پروتکلی (MPLS) مبتنی بر سوییچ برحسب Cisco است که آن نیز به نوبه ی خود از طرح سوییچینگ IP الهام کرفته است و رویکردی برای سوییچینگ بسته های IP برروی ATM است که توسط شبکه های Ipsilon مطرح شده است (Ipsilon بعدها توسط نوکیا خ…
![Cisco Voice over IP2.[taliem.ir]](https://taliem.ir/wp-content/uploads/Cisco-Voice-over-IP2.taliem.ir_.jpg)
Cisco Voice over IP2
اطلاع رسانیTo provide voice communication over an IP network, Real-Time Transport Protocol (RTP) sessions are created. These sessions are dynamically created and facilitated by one of several call control procedures. Typically, these procedures also include mechanisms for signaling events during voice calls, and for managing and collecting statistics about the voice calls. There are several types of protocols used within Cisco Unified Communications networks. In order to select the best protocol for a specific environment, network engineers need to know all of these protocols, how they can be used, and their advantages and disadvantages. This module focuses on three protocols that are used in Cisco Unified Communications networks to implement gateways and offer call-control support for VoIP: the H.323 suite of protocols, the Media Gateway Control Protocol (MGCP), and the session initiation protocol (SIP).
![Cisco Voice over IP..[taliem.ir]](https://taliem.ir/wp-content/uploads/Cisco-Voice-over-IP..taliem.ir_.jpg)
Cisco Voice over IP
اطلاع رسانیCisco Voice over IP (CVOICE) v6.0 provides an understanding of converged voice and data networks and the challenges the various network technologies face. The course also provides network administrators and network engineers with the knowledge and skills that are required to integrate gateways and gatekeepers into an enterprise VoIP network. This course is one of several courses in the Cisco CCVP™ track that addresses design, planning, and deployment practices and provides comprehensive hands-on experience in configuration and deployment of VoIP networks.
![Cisco SAFE Implementation.[taliem.ir]](https://taliem.ir/wp-content/uploads/Cisco-SAFE-Implementation.taliem.ir_.jpg)
Cisco SAFE Implementation
اطلاع رسانیNeed for Network Security: Over the past few years, Internet-enabled business, or e-business, has drastically improved companies efficiency and revenue growth. E-business applications such as e-commerce, supplychain management, and remote access enable companies to streamline processes, lower operating costs, and increase customer satisfaction. Such applications require mission-critical networks that accommodate voice, video, and data traffic, and these networks must be scalable to support increasing numbers of users and the need for greater capacity and performance. However, as networks enable more and more applications and are available to more and more users, they become ever more vulnerable to a wider range of security threats. To combat those threats and ensure that e-business transactions are not compromised, security technology must play a major role in todays networks. The closed network typically consists of a network designed and implemented in a corporate environment, and provides connectivity only to known parties and sites without connecting to public networks. Networks were designed this way in the past and thought to be reasonably secure because of no outside connectivity.
![IPS60StudentGuide Vol2 UnEncrypted.[taliem.ir]](https://taliem.ir/wp-content/uploads/IPS60StudentGuide-Vol2-UnEncrypted.taliem.ir_.jpg)
Implementing Cisco Intrusion Prevention Systems
اطلاع رسانیSensor Configuration: This topic explains how to tune the sensor to avoid evasive techniques and provide networkspecific intrusion protection. “Tuning” is a general term that is applied to the process of setting up a sensor in such a way that it provides the correct level of information necessary for protecting your specific network. If your sensor is to serve you efficiently, you must determine what level of events you want from the sensor and what you are going to do with that event information. A sensor can provide information on network events at as low a level as reporting every HTTP connection attempt or every ping sweep or port sweep, but if you have no intention of using this data, there is little reason to collect it. One of the main purposes of tuning is to modify the sensor system behavior so that the alarms that are generated have a much higher fidelity, or likelihood of being correct, and a lower chance of reflecting anything other than a true event. Another purpose of tuning is to quickly and efficiently identify attacks in progress in order to respond to them. For tuning to be successful, you must be knowledgeable about your network and the individual devices that the sensor is protecting. It is also important to have a good understanding of the protocols used on your network; it is especially important to understand the protocol inspected by any signature that you intend to tune. This knowledge enables you to recognize normal versus abnormal network activity.
![CCSP-Cisco SAFE Implementation Student Guide .[taliem.ir]](https://taliem.ir/wp-content/uploads/CCSP-Cisco-SAFE-Implementation-Student-Guide-.taliem.ir_.jpg)
Cisco SAFE Implementation
اطلاع رسانیOver the past few years, Internet-enabled business, or e-business, has drastically improved companies’ efficiency and revenue growth. E-business applications such as e-commerce, supplychain management, and remote access enable companies to streamline processes, lower operating costs, and increase customer satisfaction. Such applications require mission-critical networks that accommodate voice, video, and data traffic, and these networks must be scalable to support increasing numbers of users and the need for greater capacity and performance. However, as networks enable more and more applications and are available to more and more users, they become ever more vulnerable to a wider range of security threats. To combat those threats and ensure that e-business transactions are not compromised, security technology must play a major role in today’s networks. The closed network typically consists of a network designed and implemented in a corporate environment, and it provides connectivity only to known parties and sites without connecting to public networks. Networks were designed this way in the past and thought to be reasonably secure because there was no outside connectivity.


